
How to Find Macs with Remote Login Enabled and Disable it
Remote Login is essentially a Remote SSH server which can reduce the security of your Macs.
What Is Remote Login?
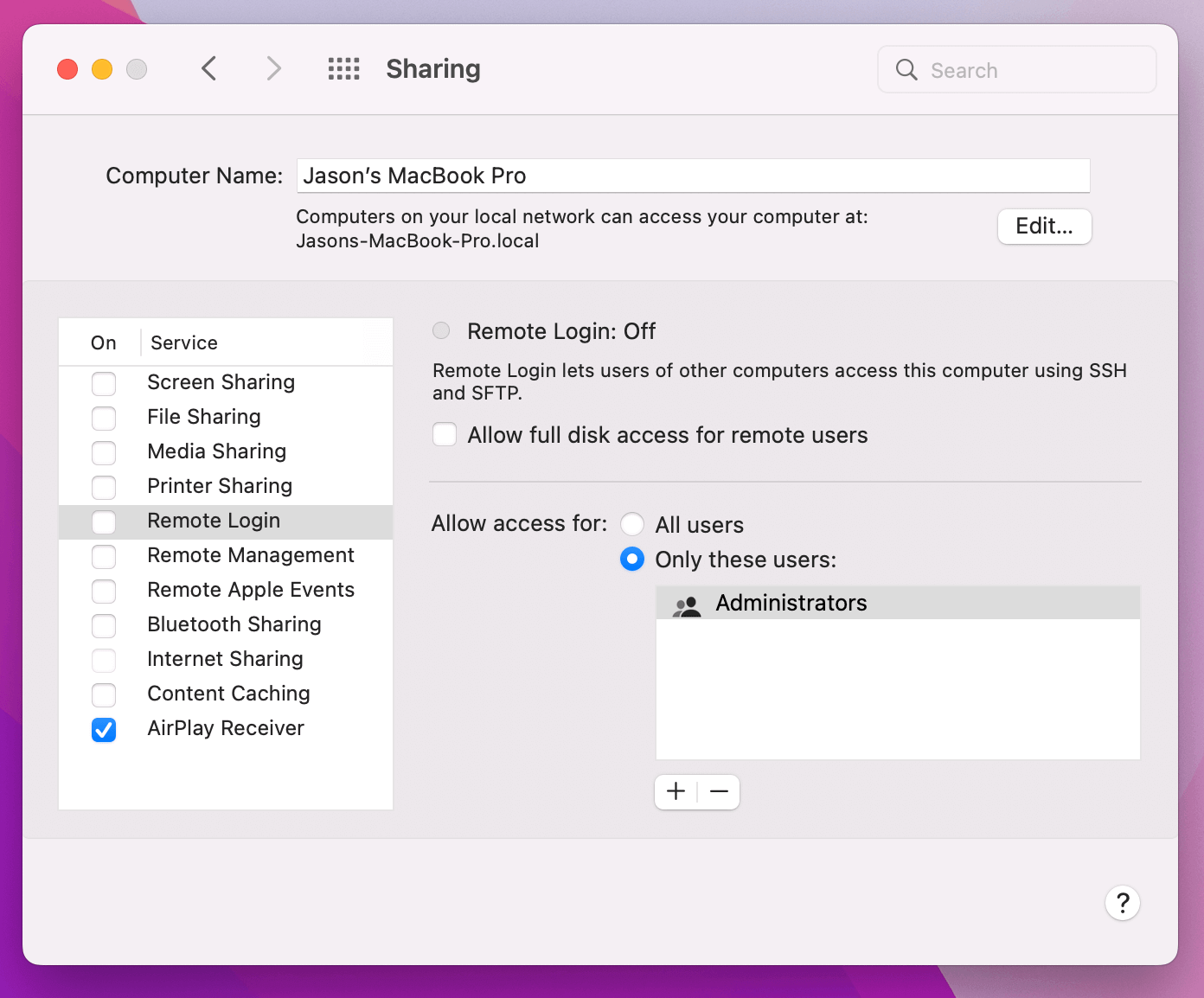
On macOS, individual users can enable a feature called Remote Login that allows them to login remotely to a device using their username and password.
Why Do Users Enable Remote Login?
In practice, this setting is rarely enabled intentionally. That being said, end users may choose to turn it on in situations where they want to access work resources from a remote location, or in situations where they are not able to bring their Mac with them. For example, perhaps they want to do work from home but they can only access a privileged network within an office. By tunneling through their work computer, they can effectively work remotely (at considerable risk to the organization). Employees that do this are also more likely to transfer the contents of work files to their personal devices.
Unfortunately, beyond the over-eager employee, there can be other more nefarious reasons this setting may be enabled. For example, it is common for illegitimate computer repair companies to ask end users to remotely enable both the Remote Login and Remote Access features of the Sharing Preferences. This is typically part of a convoluted scam that ultimately ends up with the user’s private files being exfiltrated from the device, or worse.
It’s important to remember that it’s very unlikely this setting is enabled for legitimate reasons other than remote access by technical users. So if you find it enabled on a company device, you should immediately follow up with the end user.
Why Does Remote Login Make Your Mac Less Secure?
According to Apple’s Official documentation…
Allowing remote login to your Mac can make it less secure.
When you enable this feature, macOS automatically starts an OpenSSH sever that listens on the public internet over port 22. Malicious actors have automated bots that scour the internet across all known public addresses looking for SSH servers so they can do the following:
- Look for a vulnerable SSH version (and run an exploit payload)
- Brute-force the username/password to gain access
- Retain the IP address to attack the Mac in the future when new vulnerabilities are discovered
Essentially, if you have this feature on, you are painting a big target on the back of your Mac for the minimal benefit of remote access (which may not even be permitted by the IT team). It’s not worth it.
How Do I Detect If Remote Login is Enabled?
When you enable Remote Login it simply enabled a pre-existing launchd service
called com.openssh.sshd. You can use the output of the launchctl list
command to see the status is disabled.
Detecting Remote Login With Command Line
sudo launchctl list com.openssh.sshd
When Remote Login is disabled, the command only returns the error
Could not find service "com.openssh.sshd" in domain for system. If it is
enabled, it returns the plist (in NeXTSTEP format) like the following:
{
"Wait" = false;
"Sockets" = {
"Listeners" = (
file-descriptor-object;
file-descriptor-object;
);
};
"LimitLoadToSessionType" = "System";
"StandardErrorPath" = "/dev/null";
"Label" = "com.openssh.sshd";
"inetdCompatibility" = true;
"OnDemand" = true;
"LastExitStatus" = 0;
"Program" = "/usr/libexec/sshd-keygen-wrapper";
"ProgramArguments" = (
"sshd-keygen-wrapper";
);
};
Using this method, you can write a script by examining the exit code of the command.
#!/bin/sh
sudo launchctl list com.openssh.sshd &> /dev/null;
if [ $? -eq 0 ]
then
echo Remote Login is Enabled
else
echo Remote Login is Disabled
fi
Detecting Remote Login With Osquery
You can also use an open-source tool like osquery to determine the status of this and other sharing preferences (Kolide actually contributed this specific table to the project!).
SELECT remote_login FROM sharing_preferences;
+--------------+
| remote_login |
+--------------+
| 0 |
+--------------+
Kolide’s endpoint agent includes osquery’s functionality and automatically stores all information about Remote Login and other macOS settings its built-in Inventory. Using Kolide, you can easily locate all the devices with this feature enabled.
How Do I Disable This Feature?
There are two viable (but imperfect) approaches for disabling macOS’ remote login service.
Mobile Device Management (MDM)
if you use an MDM product like Apple Business Essentials,
you can disable the entirety of the Sharing section in System Preferences with a
.mobileconfig profile (using the payload below).
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>DisabledPreferencePanes</key>
<array>
<string>com.apple.preferences.sharing</string>
</array>
<key>PayloadDescription</key>
<string>Configures System Preferences settings</string>
<key>PayloadDisplayName</key>
<string>System Preferences</string>
<key>PayloadIdentifier</key>
<string>com.github.erikberglund.ProfileCreator.476DA8E1-8450-4375-A8C0-37232350AC54.com.apple.systempreferences.1094143C-191A-41F0-B245-25DEF3760770</string>
<key>PayloadOrganization</key>
<string></string>
<key>PayloadType</key>
<string>com.apple.systempreferences</string>
<key>PayloadUUID</key>
<string>1094143C-191A-41F0-B245-25DEF3760770</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</array>
<key>PayloadDescription</key>
<string>Disables just the Sharing pane in System Preferences</string>
<key>PayloadDisplayName</key>
<string>Disable Sharing</string>
<key>PayloadIdentifier</key>
<string>com.github.erikberglund.ProfileCreator.476DA8E1-8450-4375-A8C0-37232350AC54</string>
<key>PayloadOrganization</key>
<string>Kolide</string>
<key>PayloadScope</key>
<string>System</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>476DA8E1-8450-4375-A8C0-37232350AC54</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>
Instead of disabling, you can instead hide the pane by swapping DisabledPreferencePanes
for HiddenPreferencePanes in the above .mobileconfig plist.
While this can be used to prevent a user from using this feature in the UI, it cannot be used to turn it off once it has been enabled or if a user activated it through other means, like the command line.
The Command Line
If you are able to execute commands/scripts on your Mac remotely as root, you can turn off remote login with the following command:
sudo systemsetup -f -setremotelogin off
That being said, it is much easier and more educational if you can get your end users to disable this on their own. This isn’t just a technical problem, it’s a policy and security education opportunity.
How Does Kolide Remediate This Problem?
Automatically remediating this issue isn't necessarily the best way to go. Instead, consider following the Honest Security approach by blocking devices from authenticating to SaaS apps until they've fixed the problem.
Kolide's Okta Integration does exactly that. Onece integrated in your sign-in flow, Kolide will automatically associate devices with your users' Okta identities. From there, it can block any device that exhibits this problem and then provide the user, step-by-step instructions on how to fix it. Once fixed, Kolide immediately unblocks their device. Watch a demo to find out more.
