End Security Obstructionism With Security Automation Orchestration
At Kolide, we believe that IT folks are honest and genuinely want to help their users. We speak to IT leaders every week, and we can feel their excitement when we discuss tools that hold the promise of improving the work lives of end-users.
If this is the norm — and we genuinely believe it is — why do so many employees see IT teams as obstructors? Is it because of the tools? The organization structure? Or simply a perception issue?
Whatever the root cause, this problem is now so common that new terms have already been created to describe it since we published version 1 of Honest Security.
This is fantastic because the first step of solving a problem is identifying it, describing it, and giving it a name. End-user frustration, thy name is security.
We recently came across a fantastic article by Kelly Shortridge that looks to coin a new term called security obstructionism (SecObs). In the article, Kelly defines SecObs as policies, tools, and practices that result in outcomes that impede progress under the guise (or creating the optics) of maintaining security.
Even though Kelly uses the term with her tongue firmly planted in her cheek, we think that the underlying sentiment of the piece has significant merit.
In this piece, let’s look at the face-value of this term, how it self-perpetuates within organizations, and how you can avoid falling into the SecObs trap.
What Is Security Obstructionism?
Instead of achieving better security outcomes to support a business, SecObs causes IT teams to use security outputs as a proxy for progress. Kelly’s piece enumerates many visceral examples that are evidence of SecObs at your business, including:
Forced device restarts (as a first measure), arbitrary password resets, access approval, key rotations, and other policies that leave users unable to work.
Vulnerability management processes that create long lists of triage items, which back up workflows and impact operational efficiencies.
Manual security reviews or change approvals that block teams from shipping new code without the go-ahead from the security team.
Phishing simulations conducted with a “gotcha” mentality, creating tensions between employees and the IT team (and potentially leadership.)
Interfering with or shutting down digital transformation initiatives (e.g., no-code platforms that empower citizen developers to build and publish apps.)
Use of “insider threat” detection tools that resemble malware, such as keyloggers and screen recording.
Mandatory employee training that fails to address knowledge gaps or improve measurable security outcomes.
A culture that encourages employees to follow security rules blindly without understanding why things are done.
Essentially, any security measure that requires excessive hands-on involvement of the security and IT team has the potential to turn into SecObs tactics.
What’s Wrong With Security Obstructionism?
Now you may wonder, at least the IT team is doing something to keep a company safe… but is it?
SecObs focus on security output rather than outcomes. The misdirected emphasis can cause a company to spend a lot of time and money on busy work (e.g., locking and unlocking access, organizing superficial security training) without achieving the intended results.
The highly manual processes that drive SecObs create bottlenecks that impact employee productivity. They can also hamper digital transformation efforts that automate and democratize IT and security tasks.
Moreover, many detection and monitoring methods favored by SecObs are less than honest and transparent. Employees don’t know what agents are running on their devices and who has access to their data. The lack of trust often creates friction that can ultimately harm the company’s security.
Instead of proactively cooperating with IT, employees are more likely to go behind the security team’s back. For example, they may use personal devices to handle company data, making it harder to track and secure sensitive information.
SecObs hamstring innovation, diminish operational efficiency, erode employee trust, and even harm security outcomes.
How To Overcome Security Obstructionism
Overcoming SecObs isn’t easy because it’s baked into many existing security solutions. Many applications claim to reinforce IT security but, in effect, create roadblocks to improving security outcomes.
Companies must make conscious efforts to avoid falling into the SecObs trap. But how?
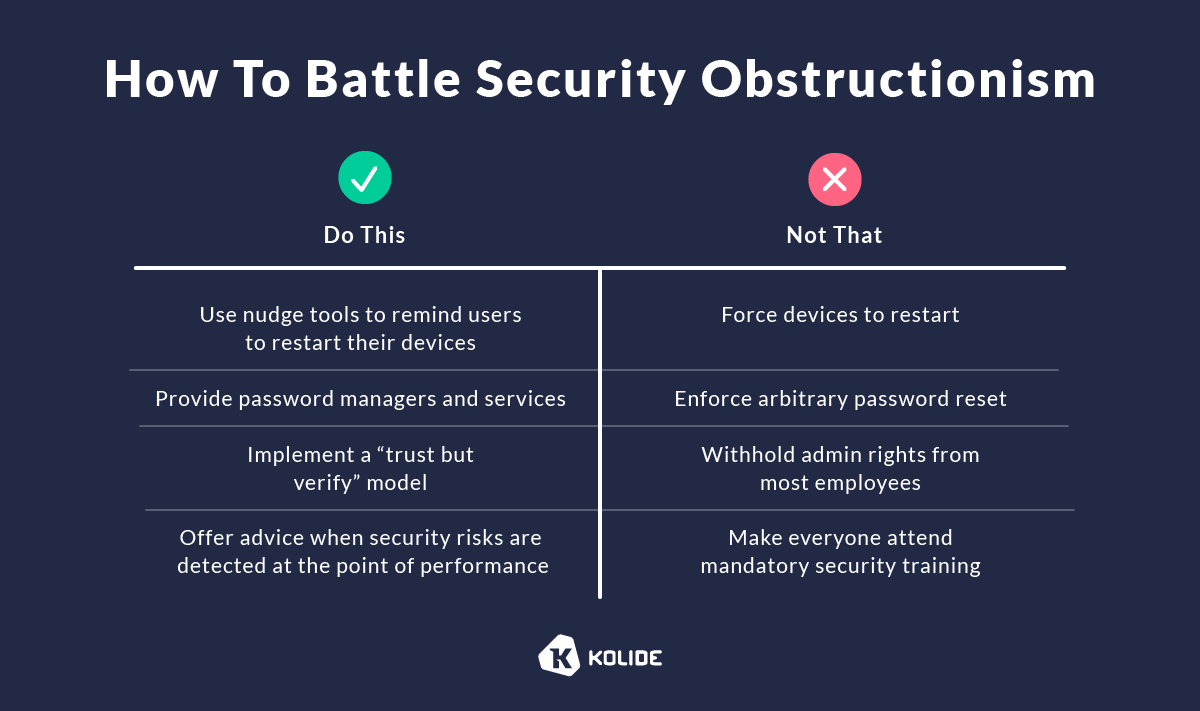
Here’s what SecObs could look like when the rubber meets the road and what to do instead:
Device Restarts
Imagine how frustrating it is if your laptop reboots when you’re in the middle of an important task. Forced device restart is not only intrusive but also impacts productivity. It conveys that the company doesn’t respect employees’ time and privacy.
Instead, use nudge tools to remind end-users to install updates and restart their devices when necessary. You can do so if you have complete visibility into your fleet and the ability to send automated messages to each employee. Only block access to devices when they ignore multiple messages and the security risks become too high.
Password Management
In the latest version of the Verizon Data Breach Investigations Report (DBIR), compromised passwords are responsible for around 81% of hacking-related breaches. Despite this and the millions of dollars and thousands of hours invested in building products and policies to solve this problem, many IT teams continue to embrace the ultimate known bad practice, arbitrary password changes.
We believe that IT and Security teams know these are wrong but are still reacting to the woefully out-of-date compliance standards that advocate for regular password rotations (even without evidence of compromise) and ill-considered (or even harmful) arbitrary password construction requirements.
Even worse, the OS vendors continue to embrace this flawed model, making it trivial for IT and Security admins to implement and automate this approach to password management and security.
Change is in the air here (especially at Apple), but password management vendors like 1Password continue to provide the best experience for end-users. They help users generate secure passwords and mitigate risk when there is evidence that a password was potentially compromised in a breach.
Administrative Rights
When you limit users’ admin rights, you could hold up critical business workflows. Employees can’t get the information they need to do their job until someone else (likely an IT team member) retrieves the data for them — a time-consuming process for both parties.
We all know deep down that using a PC or Mac without an administrative account is a profoundly frustrating experience. Why force that frustration on end-users as if they don’t have other choices? When faced with their first roadblock, many employees are not going to file a help ticket to install a tool that helps them. They will simply start using their personal devices and work around what they perceive is an arbitrary or even insulting restriction.
Instead, follow a “trust but verify” model. Grant employees admin access privilege and use a fleet visibility tool and automation technologies to detect risky behaviors and communicate remediation actions. This approach will help you increase productivity and build trust with employees — empowering them to do their job efficiently and securely.
Security Education
Imposing interruptive mandatory security training may check a compliance box but does little to bridge the knowledge gap and show employees how your security policy relates to their job functions.
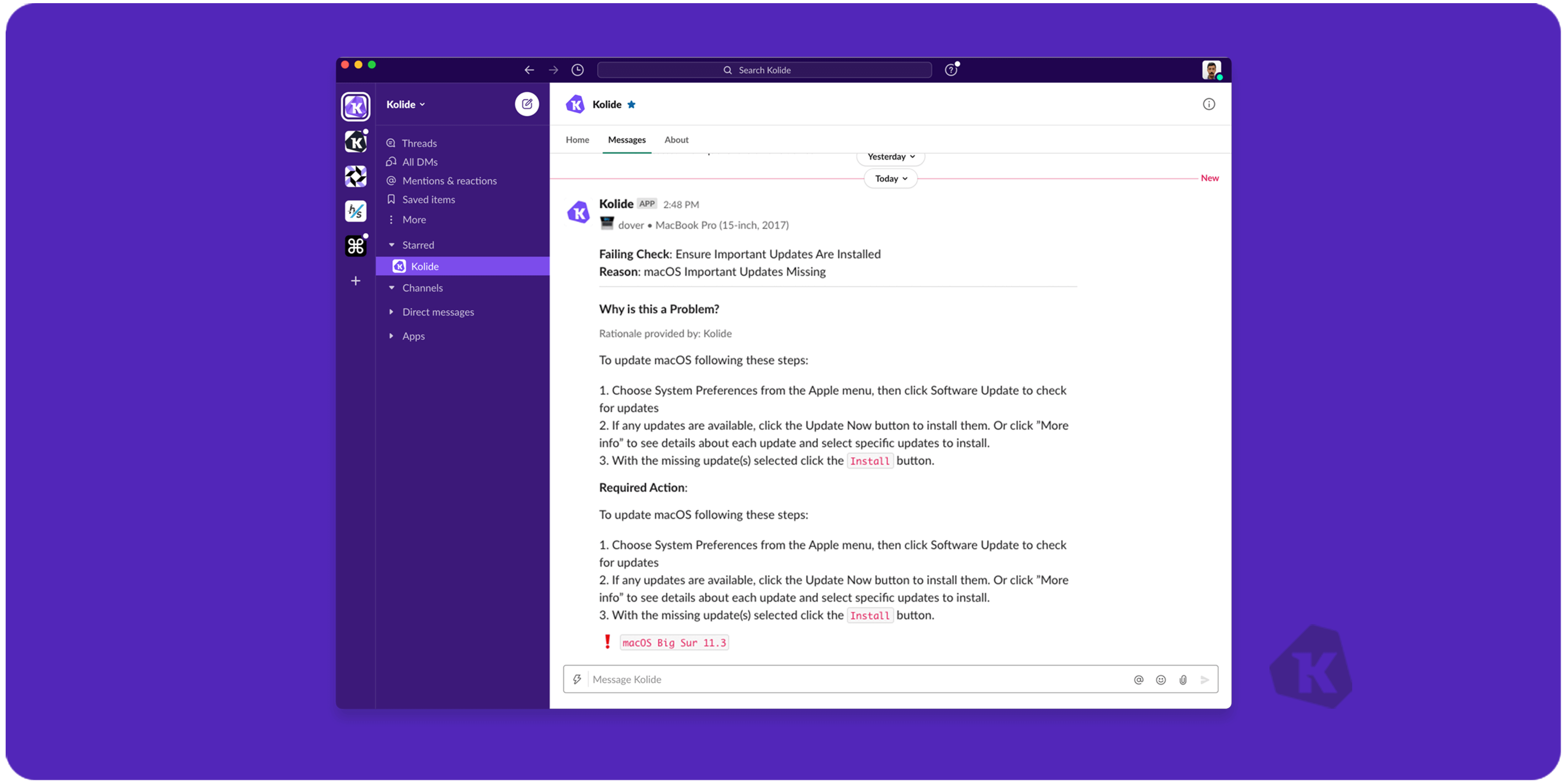
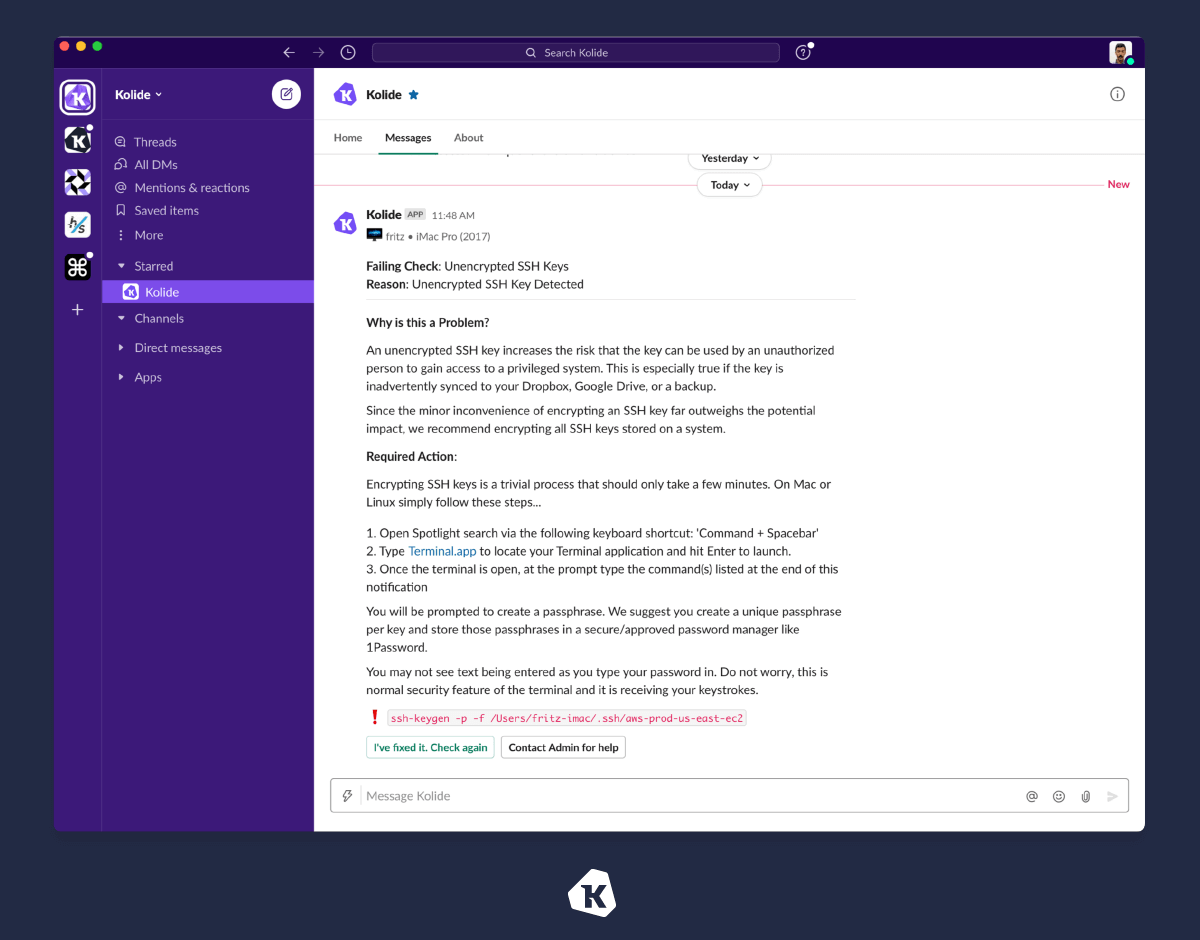
Instead, use an automated system to send personalized messages to employees regarding your security policy. Offer practical self-remediation steps at the point of performance to help end-users stay compliant with your policy when a risk is detected.

Such automation frees the security team from having individual conversations with every user when they do something that puts the company at risk. It also provides end-users with the critical information they need to learn about an issue, fix it on their own, and prevent it from happening in the future so you can improve security in the long run.
Mindset Changes To Overcome SecObs
First, IT leaders and teams must practice servant leadership. Their job shouldn’t be about “protecting the company from employees’ stupidity.” They must start from a mindset of trusting that employees will do the right thing when given the right information.
As such, you need the tools to educate employees and teach them how to take appropriate actions at the point of performance to avoid “doing something stupid,” which (ironically) is often caused by ineffective “check box” training, a hallmark of SecObs.
Next, you need to take an “outcome over output” approach to security. The truth is that in today’s fast-paced digital world, it’s not feasible to create an airtight environment. Let’s say that again for emphasis. Compromise is inevitable no matter how much you lock down your users’ devices.
At some point in the road of trying to mitigate every potential threat to zero likelihood, you encounter significant diminishing returns and begin to disproportionally hamstring your fellow employees. The key is to recognize when that balance shifts and start thinking about preparing your organization to detect and respond to the highest impact risks when they become realized in an actual incident.




