How to Store Your 2FA Backup Codes Securely
You know that creating a strong password is no longer enough. So you followed cybersecurity best practices and turned on two-factor authentication (2FA) — you’re all set, right?
Wait, don’t get too excited yet! 2FA is a critical security feature, but ironically, it also creates security risks if the backup codes aren’t stored properly.
TL;DR: 2FA recovery codes can be used as your login credentials. Not storing them securely is like leaving the key in the lock of your front door!
Read on to find out the security challenges posed by 2FA and how to store your backup codes properly.
2FA Creates New Security Challenges
Let’s start with a refresher on how 2FA works: 2FA strengthens access security by requiring users to provide two forms of authentication to verify their identities.
Authentication is the process of proving your identity by providing something you know, something you are, or something you have. 2FA requires users to meet two of these criteria. Username and password are the “things you know.” And we need to layer “something you have” or “something you are "on top of these credentials.
This is often done through the use of a time-based one time password (TOTP) code sent or generated on a user’s mobile device ("something you have”). It’s typically a 6-digit numerical strand that expires after 30 seconds.
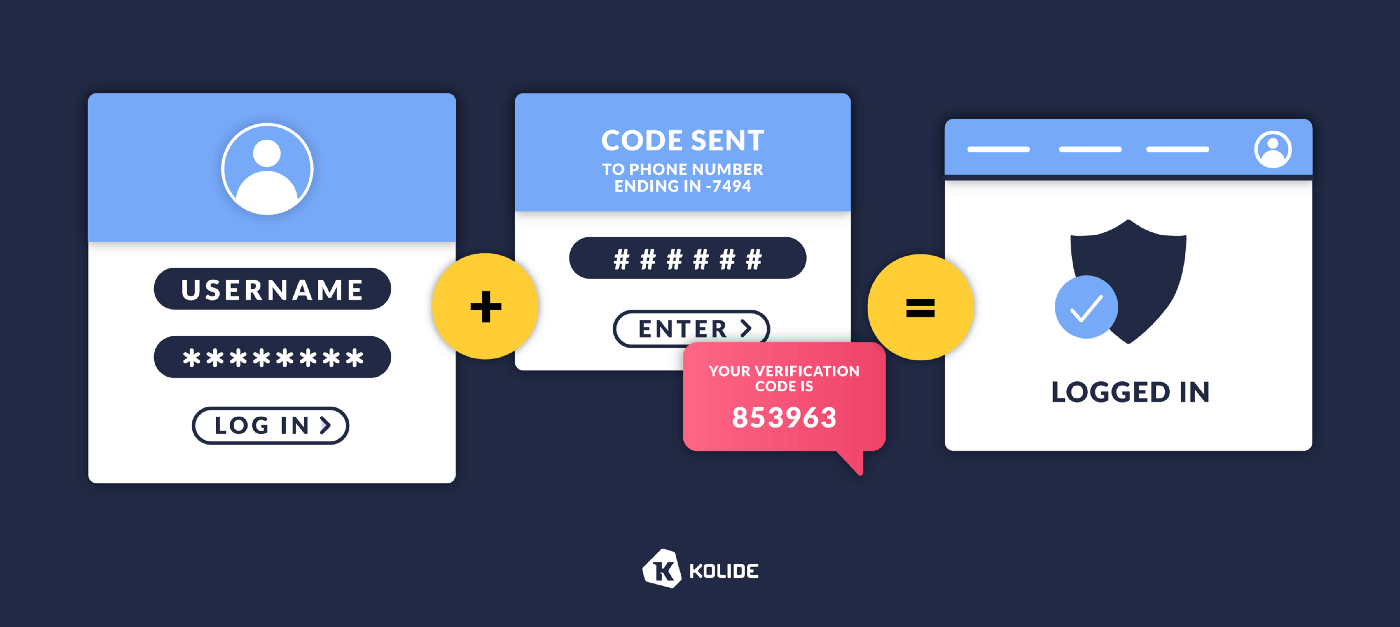
When you set up 2FA for a service, you’d enter a one time setup code into an authenticator app (e.g., Google Authenticator or FreeOTP.) This will allow you to generate TOTP codes to access the application in the future.
Some 2FA authenticators are cloud-based (e.g., 1Password or Authy). They give you the added benefit of accessing your authenticator from multiple devices, sharing with teammates, and having a backup copy of your authentication code.
You can also generate one-time use backup codes (also called recovery codes) that don’t expire. They can be used in place of the TOTP codes if you don’t have access to your authenticator.
To recap, there are 3 different types of codes involved in 2FA — the one-time setup code (or seed), TOTP, and backup codes — all with their own benefits but also weaknesses that can potentially be exploited by hackers.
If a hacker manages to retrieve a one-time setup code (e.g., from an employee’s device,) they can use it to generate TOTP codes. While they still need your account credentials to gain access, your 2FA is rendered useless and the hacker is one step closer to breaching your account. How can you be certain that employees’ devices used to generate the one-time setup codes are secure?
2FA authenticator apps typically have strong security, but are only as secure as the device they’re stored on. Threat actors can hack insecure devices to gain access privilege to multiple platforms, including authentication codes.
Meanwhile, we also have to consider how the backup codes are stored — they don’t expire, so hackers who manage to get their hands on the codes can bypass the TOTP requirement!
After employees have generated the recovery codes, they’ll need to keep them in a safe place. Can you count on everyone to keep the information secure at all times?
2FA is only as secure as the devices employees use to store and access their codes. If hackers manage to gain access to a device (e.g., by intercepting messages or installing malware,) your 2FA method would be rendered useless.
How To Securely Store Your 2FA Backup Codes
Since 2FA recovery codes are static information that doesn’t change after it’s been generated, you must ensure that they’re stored securely. Otherwise, hackers can steal them and use them to access your accounts.
If you’re generating 2FA codes on your device, the old-school low-tech way may win the 2FA backup code storage game — simply print out the backup codes and store them in a safe place.
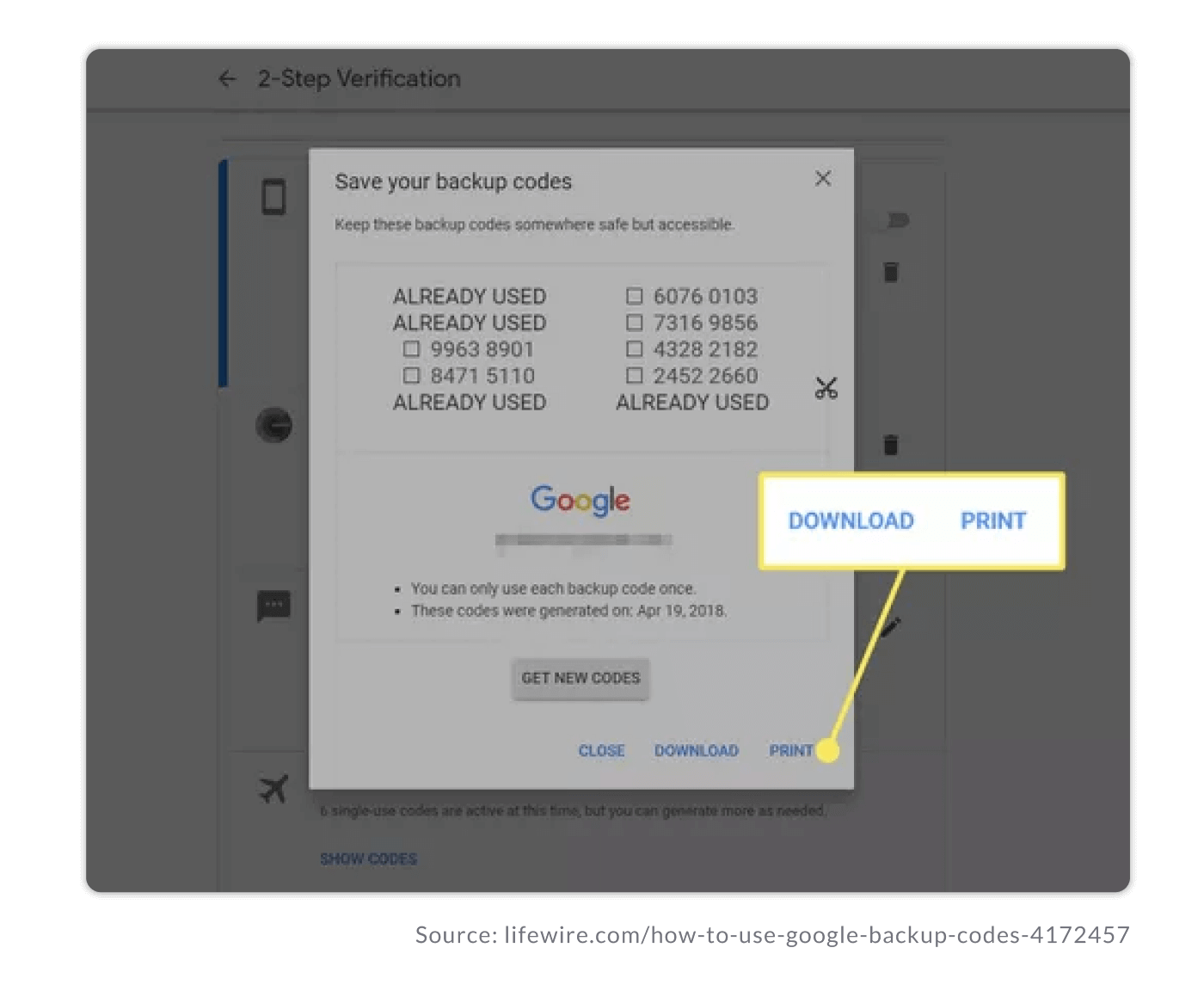
If you use a 2FA solution to streamline team access to shared accounts, you should use a password manager that will allow you to store the 2FA backup codes as notes or file attachments. Then, you must ensure that the recovery codes to the password manager (e.g., 1Password Recovery Kit) are secure, for example, by printing them out and storing them in a safe place separate from your devices or where you access login credentials.
2FA can be bypassed if you don’t store the recovery codes securely. For example, employees print out the codes and leave them in an unsecured place or use their devices to generate backup codes and then leave the information on their desktops unencrypted.
How To Choose the Right Solution For Accessing and Storing 2FA Codes
Your storage solution should offer a balance of security and ease of access. Here are some key considerations when deciding how best to store your 2FA access and backup codes:
Will more than one person need regular access to the account?
What’s the process of incorporating a new device into the workflow?
How many people and devices need access?
How can you ensure that each device set up to generate TOTP is up-to-date (e.g., have the latest security patches installed)?
How many accounts need remote access?
Has your organization suffered attacks on staff accounts in the past? What are the risk factors and the likelihood of it happening again?
If you use a remote solution, how can you prevent unauthorized personnel from requesting access from a new device?
If you can’t block access requests, how can you verify them to protect the channels (e.g., email, phone) from hijacking?
The Weak Link in 2FA Backup Code Security
One of the easiest ways for hackers to steal 2FA recovery codes is by exploiting vulnerabilities in endpoint devices (e.g., laptops, smartphones.) Then, they steal backup codes or login credentials improperly stored on them.
The proliferation of devices and the number of platforms organizations use to conduct business activities don’t make things easier. It’s challenging for IT teams to chase down every device to ensure that patches are installed, and login credentials and backup codes aren’t stored locally.
That’s why more companies are using endpoint security solutions to manage accounts and 2FA. They help you find improperly stored backup codes and ensure that all the devices have the latest security updates installed automatically. You can gain a bird’s-eye view of all devices connected to your network and their status to identify vulnerabilities (e.g., outdated operating systems.)
Kolide takes endpoint security to the next level by helping you crowdsource your defense. You can send automated notifications to employees to educate them about your security policy and provide solutions, such as identifying insecurely stored 2FA backup codes and offering step-by-step guidance to remove them from the device.
Watch our on-demand demo to see how our Device Trust solution can help you minimize endpoint security risks.