Kolide Launcher: Osquery Deployment Made Easy
At Kolide, we have a lot of experience deploying and using osquery. We want to use this experience to make deploying and managing osquery fleets easier than ever.
As an engineer at Facebook, I conceptualized and created osquery. Later, I managed the deployment of osquery to the entire Facebook fleet as the leader of Facebook’s Intrusion Detection Infrastructure team. My cofounder, Zach Wasserman, was a core contributor to osquery at Facebook, and went on to found a consulting company developing (and open-sourcing) custom osquery integrations for Silicon Valley customers.
Osquery is founded on the idea that instrumentation should be open and audited. It’s not reasonable for a security company (or any company) to ask users to install powerful, opaque rootkits. We founded Kolide to leverage our experience with osquery over a wide-range of enterprises and empower a more open, secure internet.
Today we are open-sourcing our osquery launcher because we stand by these principles of openness.
The Kolide Launcher is a lightweight manager runtime for osquery which offers extra capabilities and quality of life improvements that make deploying and using osquery easier and more scalable, for organizations of any size.
Automatic Updates
The first, perhaps most notable capability that the Launcher adds is secure automatic updates of the osquery binary as well as the Launcher binary itself. Osquery is statically linked and that allows for the easy bundling and distribution of the software. But this also requires users to maintain excellent update hygiene in order to take advantage of emerging capabilities. The Launcher includes the ability to securely manage and autoupdate osquery instances. This is implemented using The Update Framework (TUF). TUF defines a specification for secure software update systems. The specification describes a client/server model in which the client is the software to be updated and the server is the update server. For our implementation, we use Docker Notary as our TUF server and a Go client library that we built in-house. Because we understand the security implications of an osquery auto-updater, we contracted with NCC Group to perform a security audit of our in-house TUF client library. NCC Group has also performed assessments on Docker Notary and Osquery itself.
New Remote Plugin: gRPC
Next, Launcher also adds a new set of remote plugins for osquery that establish a typed server specification. Osquery has a very extensible plugin architecture that allow it to be heavily customized with plugins. The Launcher includes a set of gRPC plugins for remote communication with a gRPC server. The server specification is independently published and versioned. An implementation of the gRPC server is included with the Kolide Fleet osquery fleet manager. Kolide Fleet implements both the gRPC server as well as the existing TLS server API, so it presents an easy migration path for existing TLS API users.
Use-Case Driven Tables
It can be hard to know questions to ask and what queries will expose the
answers. These new tables provide immediate insights into aspects of concern
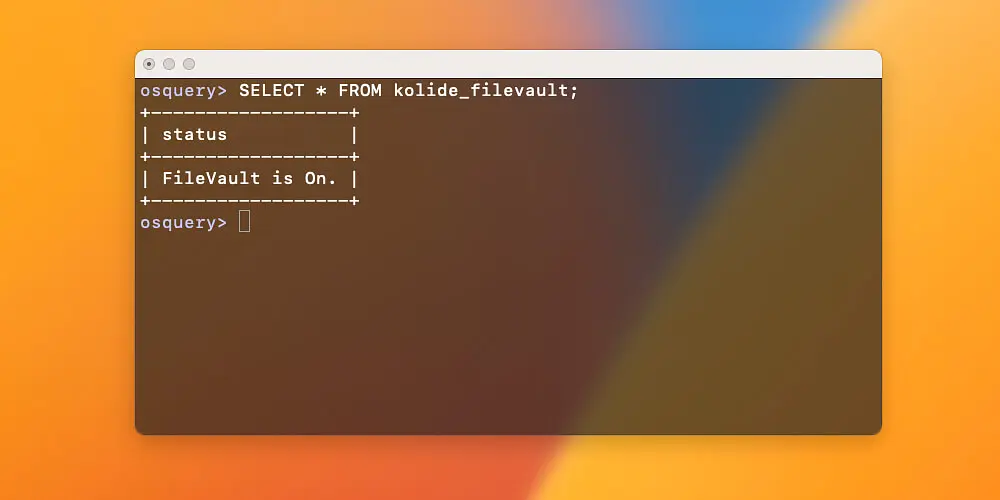
on macOS systems.The Launcher includes a kolide_best_practices table which
aggregates useful information in an easy “compliant” vs. “non-compliant”
interface. Also included is a kolide_vulnerabilities table which Launcher
populates with active vulnerabilities found on the host.
Reduced Configuration Surface
The launcher also provides a dramatically reduced configuration surface. The Launcher wraps osqueryd configuration and exposes very high-level options that allow you to easily connect osquery to a server that is compliant with the gRPC specification ( such as Kolide Fleet). This means that connecting Launcher to Fleet requires only two flags: server hostname and secret. To learn about The Launcher’s command-line interface, see the documentation for the Launcher command. Compare this with over a dozen flags required to connect raw osquery to a TLS server.
Tooling For Custom Package Generation
Finally, Deploying osquery and configuring it to communicate with a management server can be complicated, especially if you have to make customized deployment packages. The Launcher includes a tool called package-builder which you can use to create no-fuss Launcher packages for your organization.The options and capabilities are documented on GitHub.
We hope that Launcher makes your life easier. An implementation of a compatible server is included with the Kolide Fleet osquery fleet manager. Please reach out with questions in the #kolide channel in osquery slack. The source code and documentation is on GitHub at https://github.com/kolide/launcher.