Recently Discovered Evil Chrome Extensions
On December 16th, Threat Intelligence researches from Avast discovered several browser extensions that contained privacy invading malware. Read the press release here.
In the press release, Avast summarizes the embedded malware’s capabilities in the following paragraph.
Users have also reported that these extensions are manipulating their internet experience and redirecting them to other websites. Anytime a user clicks on a link, the extensions send information about the click to the attacker’s control server, which can optionally send a command to redirect the victim from the real link target to a new hijacked URL before later redirecting them to the actual website they wanted to visit. User’s privacy is compromised by this procedure since a log of all clicks is being sent to these third party intermediary websites. The actors also exfiltrate and collect the user’s birth dates, email addresses, and device information, including first sign in time, last login time, name of the device, operating system, used browser and its version, even IP addresses (which could be used to find the approximate geographical location history of the user).
In response, Kolide has created a new Check called Evil Chrome Extension - Browser History Sniffer which detects all reported compromised Chrome extensions from the Avast report. We suggest immediately enabling end-user notifications on this Check .
If users have one or more of any extensions, they will receive a notification that looks like the following:
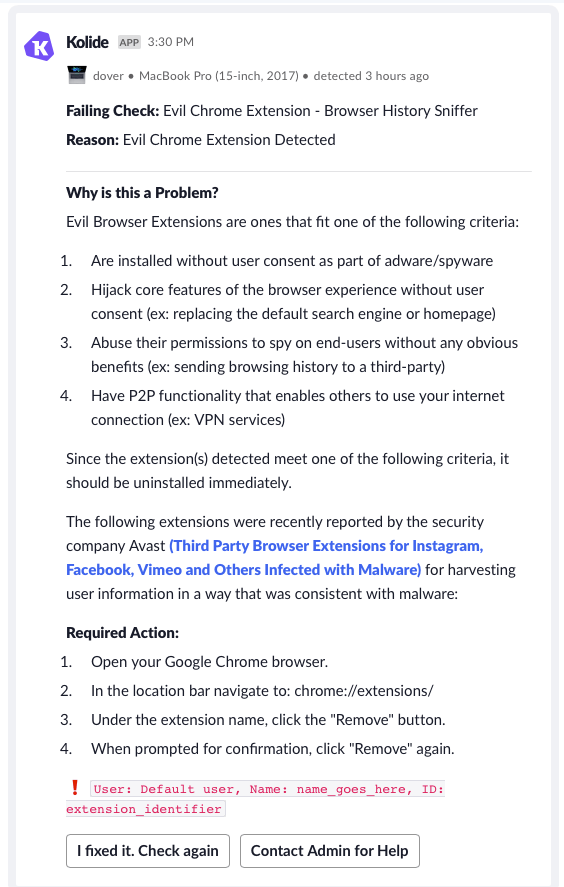
If you have any questions or concerns about this check, please reach out to us at support@kolide.co or via the Intercom widget on the bottom-right corner of the Kolide application.
For your convenience, below is a list of the Chrome Extension identifiers extracted from the links in the press release.
mdpgppkombninhkfhaggckdmencplhmg fgaapohcdolaiaijobecfleiohcfhdfb iibnodnghffmdcebaglfgnfkgemcbchf olkpikmlhoaojbbmmpejnimiglejmboe bhfoemlllidnfefgkeaeocnageepbael nilbfjdbacfdodpbdondbbkmoigehodg eikbfklcjampfnmclhjeifbmfkpkfpbn pfnmibjifkhhblmdmaocfohebdpfppkf cgpbghdbejagejmciefmekcklikpoeel klejifgmmnkgejbhgmpgajemhlnijlib ceoldlgkhdbnnmojajjgfapagjccblib mnafnfdagggclnaggnjajohakfbppaih oknpgmaeedlbdichgaghebhiknmghffa pcaaejaejpolbbchlmbdjfiggojefllp lmcajpniijhhhpcnhleibgiehhicjlnk