Windows 11 Security: What You Need to Know (22H2 Update)
It’s been a year since Microsoft released Windows 11, with the promise that it was “designed to meet the new security challenges of hybrid work.”
The first major update, Windows 11 22H2, was released in September 2022, and it goes even further to protect end users against cyberattacks and to help organizations implement a zero trust security architecture.
So here’s what you need to know about the current state of Windows, featuring the biggest features from Windows 11 and the subsequent updates.
Notable Windows 11 Security Features
It’s been a year since Windows 11 was released, so what’s the verdict?
Most IT professionals find the OS much more secure than Windows 10, especially for a distributed workforce. And the new 22H2 updates build on 11 by enabling more features by default. Here’s a quick look at the features that people find most useful:
Phishing Protection
Microsoft is trying to nudge users away from password-based authentication, but in the meantime, it’s taking an aggressive stance against phishing. The 22H2 update notifies users when they share credentials with a site that is known to be malicious. Windows will also notify users who re-use corporate credentials. Finally, users will get a notification (which is also logged in Microsoft Defender) if they save passwords in Office applications like WordPad or Notepad.
Secured-core PC Standards
Microsoft made its secured-core PC standards the new baseline in Windows 11. Secured-core PCs are 60% more resilient to malware attacks than machines that don’t meet the specifications.
Virtualization-Based Security
Virtualization-based security (VBS) allows Windows to host security software in a memory region isolated from the rest of the OS. This separation provides added protection to security solutions, which are often prime targets of malicious exploits.
Now, this “core isolation” feature will be enabled by default in new devices and installations (though not for 22H2 updates on devices where it was previously disabled). Gamers are complaining that this feature hurts performance, so IT admins will want to consider whether the beefed up security is worth the productivity tradeoff.
Hypervisor-Protected Code Integrity (HVCI)
Hypervisor-Protected Code Integrity (HVCI) is a VBS feature that protects the isolated system memory environment. It prevents the Windows kernel (i.e., the brain of the OS) from being compromised, so threat actors can’t use kernel code to infiltrate the OS.
In 22H2, Microsoft is implementing Kernel Mode Hardware-enforced Stack Protection that goes further in protecting kernel code, but that update is hardware-dependent. In addition, Microsoft writes: “This setting has a dependency on HVCI (Virtualization Based Protection of Code Integrity). There shouldn’t be any issues as long as enterprises are following the baselines but, if the organization deviates from HVCI, then Kernel Mode Hardware Enforced Stack Protection cannot be enabled.”
The UEFI Secure Boot
Malicious attacks, rootkits, and unauthorized software updates can occur if a PC boots up with corrupted code. United Extensible Firmware Interface (UEFI) Secure Boot guards against exploits during system start-up by ensuring that the computer only boots up with code from a trusted source (e.g., PC manufacturer, chip maker, Microsoft.)
Microsoft Azure Attestation
Microsoft Azure Attestation (MAA) remotely verifies a platform’s trustworthiness, such as the integrity of the system’s hardware and software. This feature allows organizations to enforce Zero Trust policies to support secure access to cloud resources.
Passwordless Access
Windows Hello is Microsoft’s authentication app. Its passwordless access feature verifies a user’s identity using a PIN, fingerprint, or facial recognition. And Windows will take an even bigger step toward passwordless authentication later this year, when it joins Apple and Google in implementing passkeys.
Unfortunately, the 22H2 rollout has actually caused some problems with Hello–locking out users who already had it enabled. Microsoft promises a fix is on its way (by the time you read this it’ll probably be done) and it will block 22H2 installation on impacted PCs until then. They advise IT admins and users not to attempt a manual update before the bug fix is released.

Windows Defender Capabilities
Windows 11 includes improvements to Defender SmartScreen and Smart App Control to protect users against phishing websites and malicious apps. Meanwhile, Windows Defender Credential Guard is enabled by default on Windows 11 Enterprise. It uses VBS to isolate sensitive information, making it only accessible by privileged system software.
Account Lockout Policy Changes
22H2 offers expanded brute force attack protection, which locks the system after a certain number of failed attempts at guessing a local password. This aims to mitigate Remote Desktop Protocol (RDP) and other brute force attack techniques.
While Windows had previously offered brute force protection, it exempted local administrators from the lockout policy, which made them appealing targets for brute force attacks. Along with this update, Microsoft is also enforcing complex password requirements for local admins.
In both cases, IT admins should ensure these policies are actually enabled, since Microsoft writes that they will not necessarily be enabled by default.
Printer Security
In Microsoft’s post about 22H2 security, they write that it’s “critical to continue to protect enterprise customers in print scenarios.” This seems like a tacit acknowledgement of the “PrintNightmare” issues that plagued IT admins in Windows 10 by introducing a vulnerability in the print spooler. While the release of Windows 11 addressed the original issue, printer-related bugs have remained. In 22H2, “several new settings under Administrative Templates\Printers are enabled to further protect enterprises,” chiefly by enabling tighter security measures by default.
However, this rollout has had issues of its own. Neowin reports that IT admins have lost access to network printers after the update. “Apparently, the printer policy in the 2022 feature update was set wrong by default,” they write. “The Remote Procedure Call (RPC) connection settings need to be set to ‘RPC over named pipes’ transport protocol for the printers to be identified.”
Key Challenges and Considerations with Windows 11 Security
While Windows 11 offers many improved security features, implementing this new OS isn’t without challenges. Here’s what you should consider:
Upgraded Hardware Requirements
Windows 11 requires a PC with at least two cores, HVCI-compatible drivers, a 64-bit, 1 GHz processor, and virtualization extensions. You’ll need a device with at least an 8th generation Intel CPU, an AMD Zen 2, or a Qualcomm Snapdragon 8180 to ensure that you don’t sacrifice performance and usability for security.
These hardware specifications may require a substantial upfront investment in new devices, deterring some companies from installing the new OS.
The Risks of TPM 2.0 Bypass
Trusted Platform Module (TPM) is an international standard used in cryptoprocessors to secure hardware through integrated cryptographic keys. You need TPM 2.0 to take advantage of all the Windows 11 security and authentication features, such as Windows Hello for identity protection and BitLocker for data protection.
But many older machines aren’t equipped with a TPM 2.0 chip. To drive adoption, Microsoft published a method to bypass the TPM 2.0 requirements, allowing users to install Windows 11 on machines with TPM 1.2.
But even though Microsoft shared this bypass themselves, they strongly advise against using it. The company writes that “Devices that do not meet these system requirements will no longer be guaranteed to receive updates, including but not limited to security updates.” Furthermore, they warn that manufacturers’ warranties don’t cover damages caused by lack of compatibility.
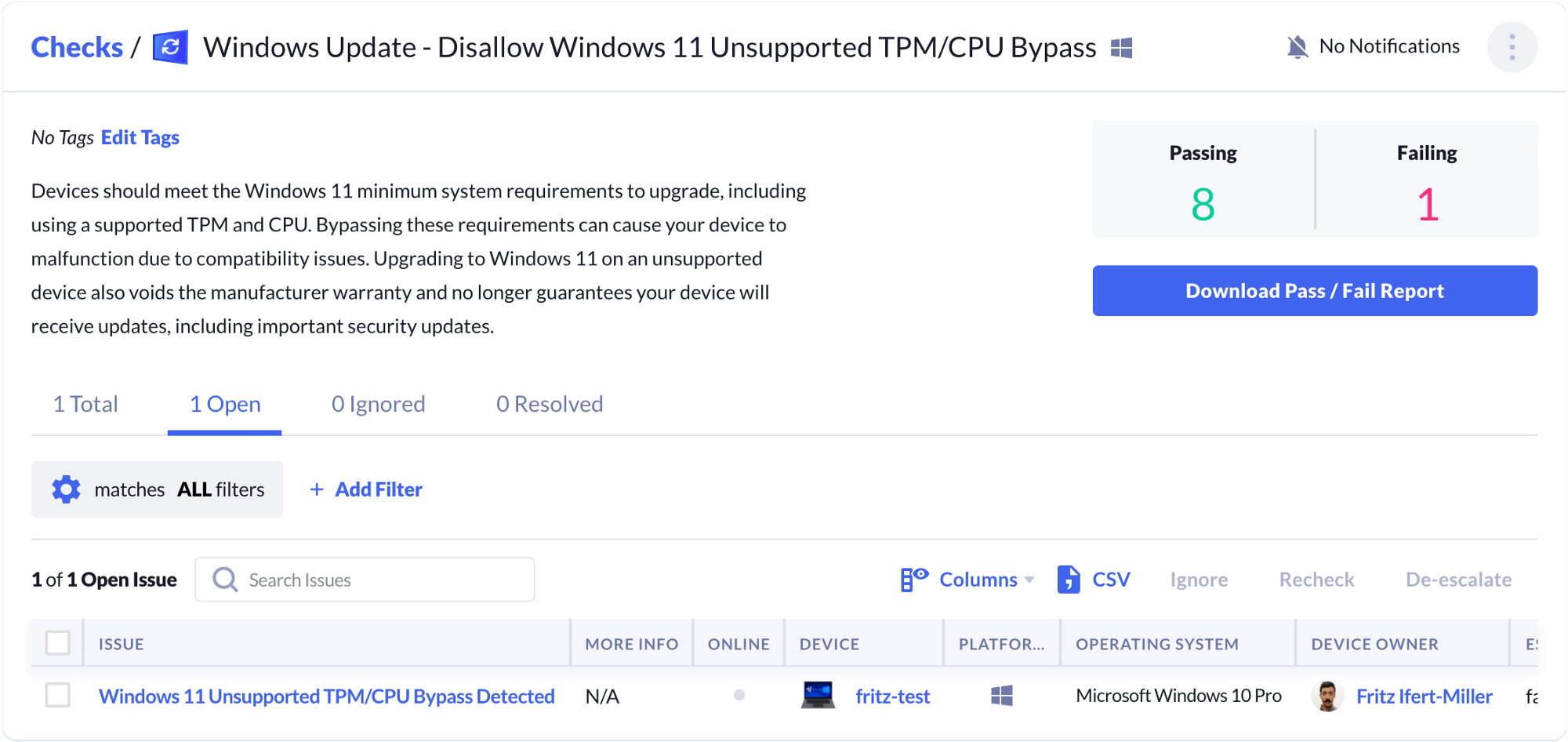
Kolide has developed a check to detect the TPM 2.0 bypass. Our software will flag devices that have bypassed the TPM 2.0 requirement so IT has insight into which machines may run into compatibility issues. It can also send automated messages to guide affected end-users to take the appropriate action, such as contacting IT for a hardware upgrade.
Interlocking Problems and Legacy Code
Microsoft has a pretty stellar record when it comes to maintaining backwards compatibility with older software–but that’s not to say there won’t be any issues with how these new security features interact with legacy software.
New Threats and Social Engineering
As always, threat actors will adapt to these new features. Well-funded Advanced Persistent Threat (APT) actors will uncover loopholes, and ransomware groups will find low-hanging fruits.
And even anti-phishing features and passwordless authentication can’t defeat social engineering schemes if end users don’t enable them. It’s up to IT admins to make sure every Windows device in your fleet is up-to-date and in compliance.
How To Make the Most of Windows 11 Security Features
Windows 11 offers many robust security features—but that’s only half the story. You also need to ensure that employees use them effectively by incorporating these best practices into your IT policy:
Keep Windows 11 up to date: Install the latest patches and bug fixes as soon as they’re available.
Use passwordless login options: Use facial or fingerprint recognition, if available, instead of a password.
Enable built-in security tools: Set security features (e.g., malware scan) to run automatically in the background.
Switch on reputation-based protection and exploit protection: Protect against suspicious apps and malware.
Manage application permissions: Configure devices to allow only trusted applications to access the device’s location, camera, and microphone.
Encrypt the data: Enable device encryption from the Windows 11 settings screen to protect data stored on the device.
While it’s easy to recommend all the steps above, putting them into practice is another matter.
Even if you use mobile device management (MDM) software to update every PC in your fleet, you must ensure that these features are indeed working as intended. For example, can you run a real-time query to see if each security feature is configured correctly on every device? And can you proactively detect if a user changes a setting? Can you see if any Windows devices in your fleet are running with an outdated TPM chip?
As you may have guessed, those are rhetorical questions–you can’t achieve that level of visibility with MDM alone. And this is where we tell you how Kolide fits into your cybersecurity big picture.
Our endpoint security solution gives you the visibility to monitor devices at scale. Our agent sends notifications to users when their device is out of compliance, so they can self-remediate issues without intervention from IT.
Watch the on-demand demo to see how our Device Trust solution can ensure that all Windows 11 security features are configured property across your entire fleet.