Why Kolide Device Trust?
Background
The number one job of IT and Security teams has always been to enable employees to do their jobs using technology resources efficiently, flexibly, and most importantly, securely.
As recently as 10 years ago, we lived in an office-centered world dominated by apps only available on private networks accessed primarily from highly predictable and managed Windows Devices. Extending that privileged network remotely was as easy as acquiring a VPN, which quickly became a natural centralization point used to control access to apps.

Read Our Blog: “Are VPNs on the way out?”
Fast forward to today and things have changed. What was once a few dozen native and intranet-only accessible apps, has exploded into thousands of SaaS apps available publicly on the internet and from any device.
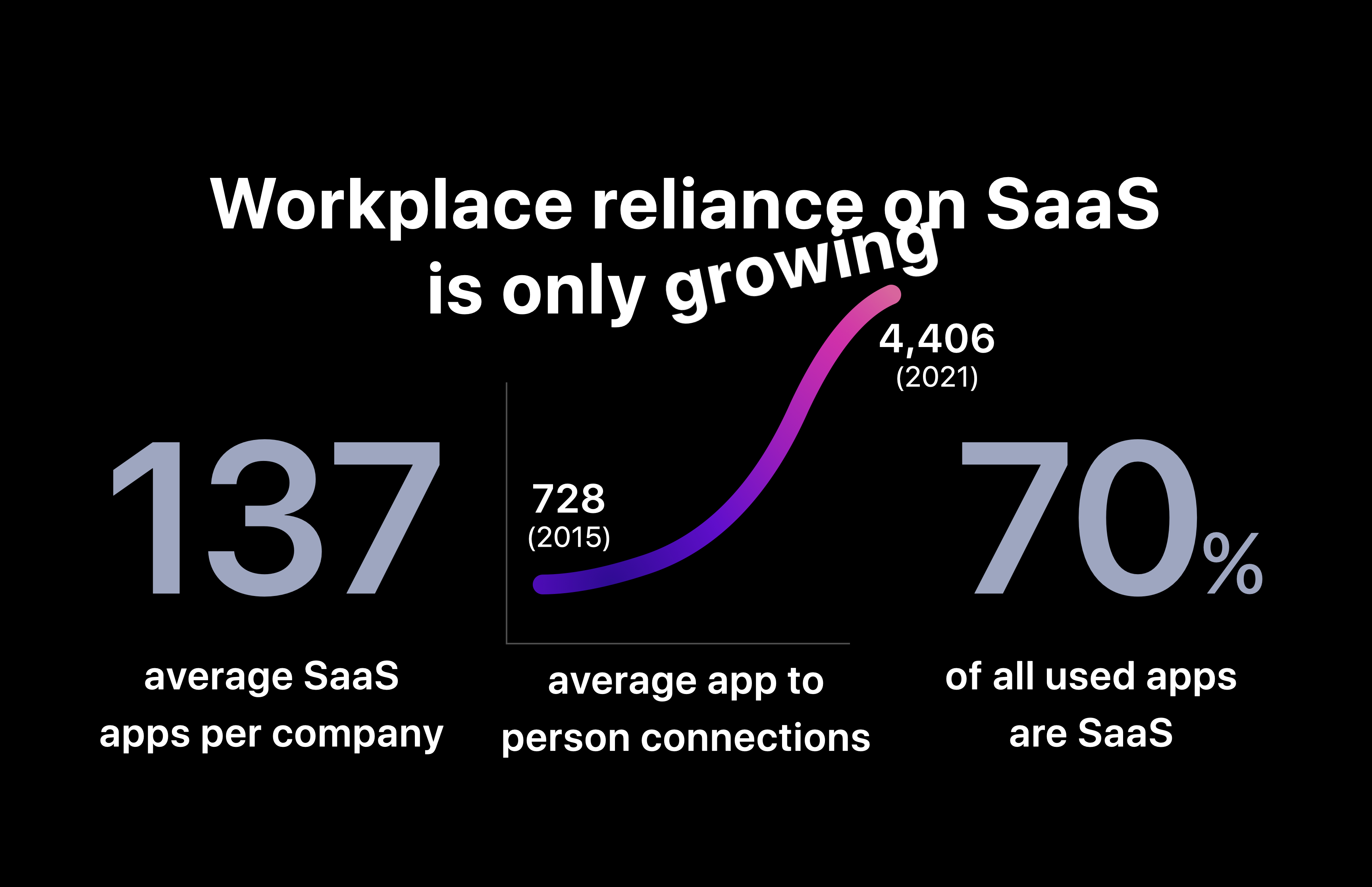
Source: “SaaS statistics: trends, data and insights from $2.5b in processed software spend” (Vendr)
While initially each app implemented its own bespoke authentication, as the number of apps increased, this became untenable. The solution was to centralize authentication by embracing Single Sign On (SSO). SSO providers like Okta have enabled organizations to deploy a consistent authentication experience across apps that meets the company’s security standards.
SSOs have evolved from their humble beginnings and now are full Identity and access platforms that enable organizations to make use of this new non-network based “choke-point” to validate far more than the identity of the user attempting to authenticate.
This is where Device Trust comes in.
Virtually every company today uses firewalls to enforce perimeter security. However, this security model is problematic because, when that perimeter is breached, an attacker has relatively easy access to a company’s privileged intranet. As companies adopt mobile and cloud technologies, the perimeter is becoming increasingly difficult to enforce. Google is taking a different approach to network security. We are removing the requirement for a privileged intranet and moving our corporate applications to the Internet.
For more information, we encourage you to read the following Kolide blog posts covering these topics in depth:
Agent-Based Device Trust Is Superior
Kolide’s Device Trust solution uses on-device software to:
- facilitate device trust,
- continuously assess a device’s posture,
- communicate critical device security and configuration telemetry to IT and security teams.
We chose this over other potential methods to ensure the highest possible quality of data, least impact on the user’s productivity, and to allow the solution to work in virtually any operating scenario.
Data Quality and Security
The benefit of running trusted software to collect endpoint telemetry is that you can be confident in the accuracy of the data.
Learn more in our article entitled, “Device Trust Architecture”
Kolide’s CEO Jason Meller writes about this in the Honest Security Guide in a section called, “The Importance of Ground Truth”:
In order for Honest Security to function properly, it must have highly accurate facts about devices, organizations, and most importantly, people. These ground truths allow Honest Security to confidently make correct security decisions/assertions and deliver them to the right people.
With superior data quality comes the ability to wield it in ways that are simply not possible using the data of other agents or basic network signals. For example, the ability to programmatically detect that software is installed, running, associated with the correct license, and self-reports as “healthy”.
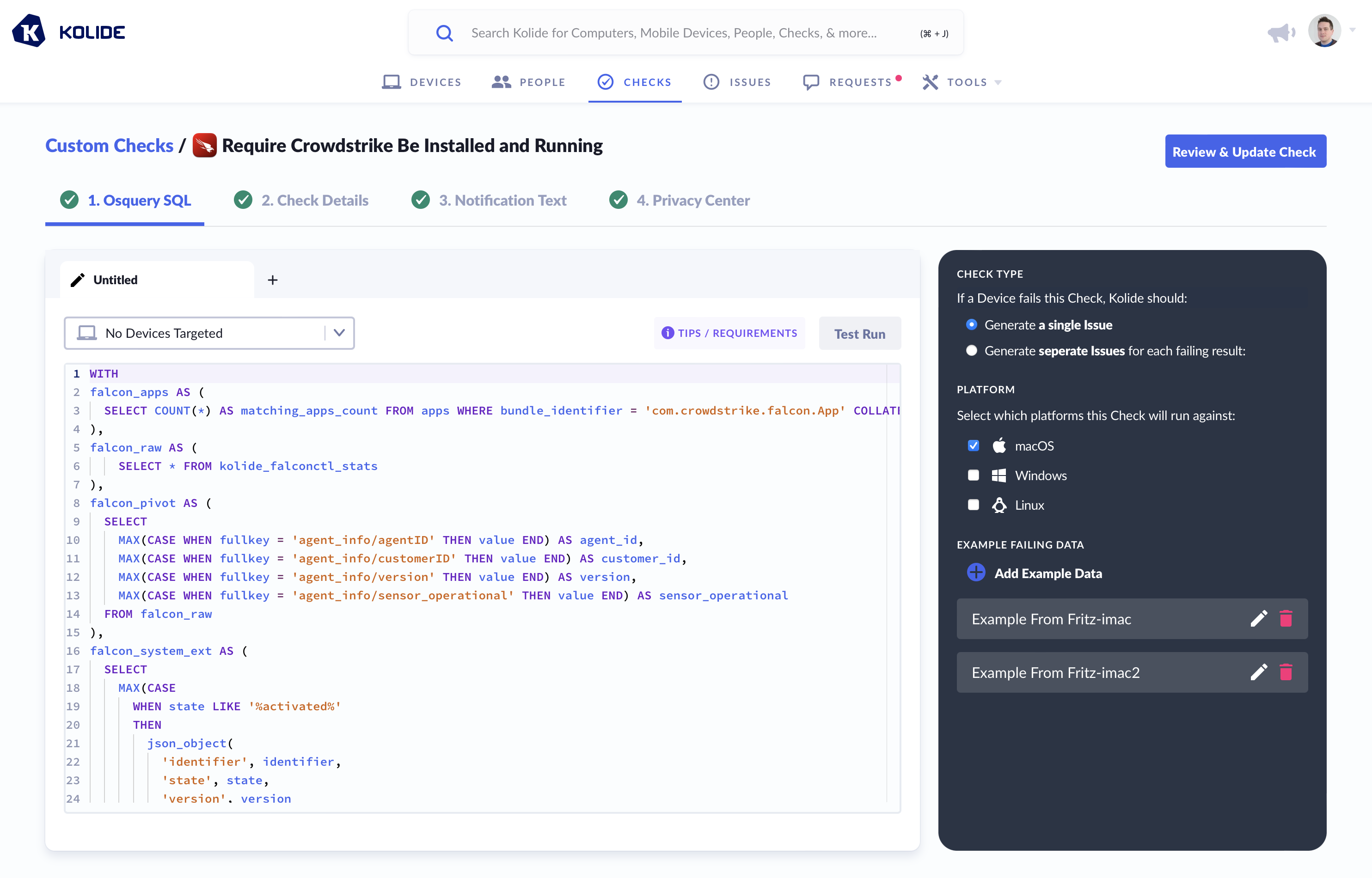
An example of Kolide’s Custom Check editor showing the Crowdstrike Check which can detect the presence of the software and even ask it to confirm its sensors are operating correctly.
Minimal User Impact and Superior UX
Many IT and Security admins conflate user impact with device impact. It’s absolutely true that software that collects device telemetry must use the system’s resources to achieve that end-goal. Fortunately, modern operating systems are now capable of managing the perceptible impact of telemetry gathering as operating system APIs to collect it become more efficient as these platforms mature and the underlying speed of the device itself improves with every subsequent hardware revision released by the device’s manufacturer.
On the other hand, what’s often discounted by IT practitioners are the User Experience (UX) impacts that seemingly lighter-touch data collection strategies generate.
For example, some VPNs often send some basic device telemetry to the central VPN concentrator (or cloud service) that’s generated by the VPN client software. Unfortunately, the mere usage of a VPN to achieve this goal requires an end-user to reason about the VPN software when doing anything important.
- How do I know when to connect to the VPN?
- Why is Zoom so laggy when I am connected?
- Why isn’t the VPN software compatible with the new major release of my operating system?
These are all examples of questions IT practitioners are used to receiving when additional cognitive load is placed on the user.
By contrast, Kolide’s agent runs silently in the background and can be installed in advance by the MDM software. Once installed and registered, end-users don’t need to do or know anything, they simply sign into their software using their SSO provider, a process they are already familiar with.
Kolide only interrupts users as an intentional feature to get them to solve serious issues Kolide detects on their device.
A short excerpt from our informational video about Okta + Yubikey + Kolide demonstrating a typical end-user sign in experience.
Real-Time Feedback
Agents allow the continuous reassessment of the device’s state. This creates instantaneous feedback loops that enable powerful use-cases like Kolide’s end-user-driven remediation.
A simulation of Kolide’s end-user driven remediation. In this workflow, the agent provides continuous assessment of the device’s state to provide positive feedback to the user when they’ve completed the task successfully.
These types of real-time experiences require low latency and secure connectivity between the UI driving the end-user’s actions and the systems that provide device telemetry.
Closing Thoughts
In summary, the increasing complexity and interconnectedness of our digital environments necessitate a nuanced approach to device security. The legacy model anchored in virtual private networks (VPNs) and other network perimeter strategies appears increasingly insufficient in meeting these demands.
In contrast, Kolide’s Device Trust solution adopts a fundamentally different perspective. Instead of working from the network inward, it directly engages with devices, using specialized on-device software to provide a harmonious user experience, effective real-time response, and minimal disruption to productivity.
By prioritizing high-quality data and accurate security information, it enables organizations to achieve an elevated degree of oversight and control. This approach, which views security as an inherent attribute of each device rather than as a peripheral consideration, offers a progressive and intelligent path forward in our quest for robust, adaptable device trust.